Challenge Information
- Platform: OverTheWire (Bandit)
- Difficulty: Easy
- Category: Linux
Overview
To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
Solution
SSH into machine on port 2220 with password from previous level.
ssh -p 2220 bandit19@bandit.labs.overthewire.org
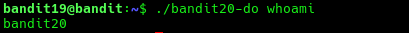
So here we are provided with a binary executable called bandit20-do. It runs a command as another user. In this case the user is probably bandit20 which we can confirm by running it with whoami.
./bandit20-do whoami
We know that the bandit20 password is located in /etc/bandit_pass directory so we can ls and check who has permission to read it.
ls -l /etc/bandit_pass/
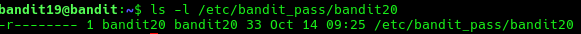
We see that it is bandit20 so we can use our binary to cat the password.
./bandit20-do cat /etc/bandit_pass/bandit20
Lessons Learned
- Running binary executables.
- Checking permissions.
Tools Used
sshlscat